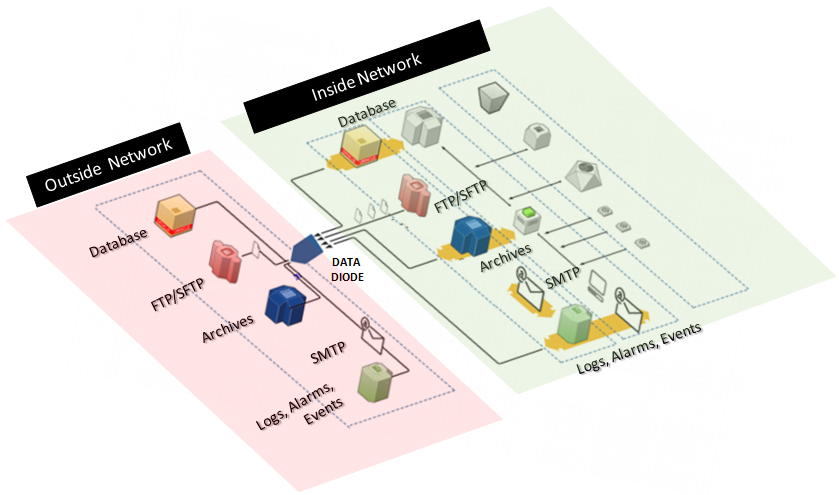
Secure “One-Way” Communication through DATA DIODE
DataDiode is an elegant solution for the high security transfer for data between networks.
DataDiode for High Security Networks
DataDiode is an elegant solution for the high security transfer for data between networks. It is a unique hardware-based, communication device, which operates in a unidirectional mode and makes use of a gigabit optical data link to transfer data in a single direction (hence the term ‘diode’), between a low-security network and a network with a high-security level. Needless to say, this solution can also be used where both networks have the same level of security
How Secure is the Solution

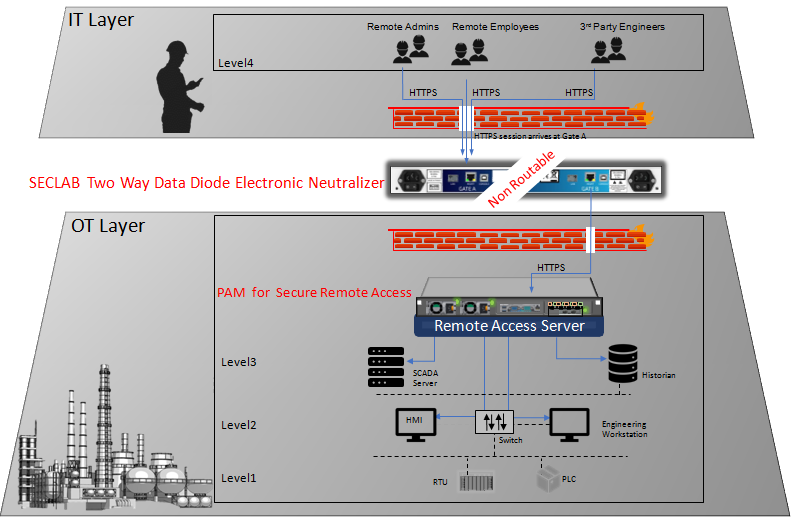
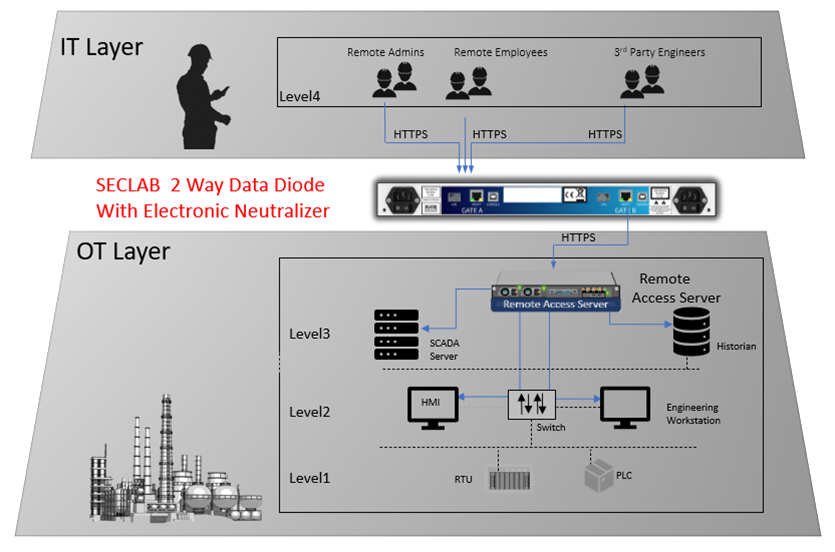
Secure Remote Access Solution
Secure Remote Access Solution through a hardware-enforced cross-domain gateway to allow controlled data exchanges (files and flows) between 2 networks.
Secured Remote Access Solution – Zero Trust !
A cyber-attack begins with a preliminary phase, which is all the more dangerous as it is most often invisible, undetectable and can last several months in this way. This is the phase during which cybercriminals collect, without your knowledge, information about your infrastructure: networks and systems (servers, PLCs, connected objects).
This preliminary phase is always present in targeted attacks (e. g. a state, a company, an installation). Unfortunately, victims only notice this after the fact because this phase is usually not detectable.
Comprehensive USB Malware SCAN Solution
We provide Security products and bespoke solutions for IT/OT convergence in Industrial environments
MULTI Antivirus KIOSK – to Scan USB Media
According to research, around 30 % of viruses come from USB devices. With our multi antivirus USB Scan solution, we ensure the data has been scanned through various antivirus engines before entering the facility and user can plug a clean in USB device with confidence.
The KIOSK analyzes and decontaminates your USB device to protect your computer and your network from USB device infections.
KIOSK is an analysis and decontamination solution for USB devices. It allows you to protect your computer from infections included in a USB device.
KIOSK is fully manageable through an On Premise or a Cloud based (SaaS) management server with access to analytics, reporting, history, etc.your computer and your network from USB device infections.
- Combines multiple Technologies, ensuring Quality Result
- Malware Detection using Numerous Antivirus Engines
- A Comprehensive Solution with 4 Layers of Security

Data Transport Media
USB SCAN KIOSK, provides a USER friendly interface where user can plug in the USB and see the SCAN progress


To Scanner


To Network

Contact Us
Want to get in touch? We would love to hear from you. Here’s how you can reach us…
